Update September 16th 2017 : I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin.
Visit the above link to update/upgrade to a hack free version with significant widget logic feature upgrades (supports more core widget logic and several popular plugins) or use the Display Widgets Plugin v4.* Direct Download Link: this link will always download the latest version filename display-widgets.zip.
December 2019 update: I’ve not updated the Display Widgets Plugin v4.* for a while, there is nothing wrong with it. I use it on this and many other websites and have received no support request, no one is having issues.
If you run Display Widgets version 2.05 (or earlier), 2.6.0 (downloads huge extra plugin), 2.6.1 (hacking code), 2.6.2 (hacking code), 2.6.2.1 (hacking code), 2.6.3 (hacking code), 2.6.3.1 (hacking code) to upgrade either:
Delete the Display Widgets Plugin under your “Plugins” menu (there’s a Delete link associated with each plugin: this won’t delete your current plugin settings) and then go to “Plugins” >> “Add New” >> “Upload Plugin” and “Browse” to the downloaded “display-widgets.zip” file and install it like you would with any plugin.
Or a manually using FTP:
Delete the Display Widgets Plugin under your “Plugins” menu (there’s a Delete link associated with each plugin: this won’t delete your current plugin settings) and then extract the “display-widgets.zip” file and use an FTP program (Filezilla for example) to upload the “/display-widgets/” folder** to /”wp-content/plugins/”.
** The zip file extracts to “/display-widgets/” within that folder is another “/display-widgets/” folder, it’s the second “/display-widgets/” folder you upload, not the first. The end result should be:
"/wp-content/plugins/display-widgets/"
NOT-
"/wp-content/plugins/display-widgets/display-widgets/"
I’ve had to support a lot of WordPress users who made the above mistake :-)
In either case the new v4+ plugin will use your old Display Widgets settings, so should work with no need to do anything, though there are new widget logic options so best to go check your widgets. Note: WPML Language plugin support has been fixed, so if you use this premium plugin you must check your widget options.
Back to the Display Widgets Plugin Reviews….
Display Widgets Plugin v2.6.* Includes Malicious Code
The Display Widgets Plugin v2.6.* includes hacking code, the WordPress Plugin team have banned the new plugin developer (@displaywidget) and closed the Display Widgets Plugin on the free WordPress Plugin Repository.
I offered the plugin team my updated version (v3.0.0), but instead they released an update which is the old v2.05 code (the last secure version) that’s been given the version number 2.7 so users of the hacked versions (v2.6.*) receive an update notification under their WordPress Dashboards. If you are running a 2.6 version, UPDATE/UPGRADE ASAP and check your site wasn’t hacked.
There’s a few bugs in the v2.05/2.7 code (it’s over 3 years since it was last updated) and the widget logic options are basic, so it’s best to update/upgrade to the new v4+ plugin from Display Widgets Plugin v4.* Download : this link will always download the latest version filename display-widgets.zip
The above update is described at Display Widgets Plugin which has more bug fixes and more widget logic features than I added to my quick v3.0.0 release. If you are running v3.0.0 it’s a safe version, but has no built in upgrade feature (v4.0.0 does), it’s recommended to upgrade to v4.0.0 to receive future updates and the new widget logic features.
In either case the new v4+ plugin will use your old Display Widgets settings, so should work with no need to do anything.
Display Widgets Plugin Reviews
Sub-topic: How I was unfairly moderated on the WordPress support forum for posting about a plugin which breaks multiple WordPress plugin repository rules and potentially damages WordPress users sites!
I’m a long term user of the Display Widgets plugin, the plugin was so usefully I added the plugin directly into the Stallion Responsive Theme over 5 years ago and last year forked** the plugin to create the Display Widgets SEO Plus Plugin.
** Forking a plugin means making a copy of it, fix bugs/add new features and possibly take the plugin in a different direction.
I forked the Display Widgets plugin (version 2.05) because the developer had stopped maintaining the plugin (over 2 years without an update, wasn’t answering support requests) AND I wanted to fix bugs and extend the Display Widgets features (v2.05 is quite basic in widget logic features).
Who Knew You Can Buy Open Source Plugins!
Around May 2017 the original Display Widgets plugin developer sold the plugin for $15,000 to a new developer (WordPress username @displaywidget).
I took the above screenshot mid July 2017, the developer has been a member of the WordPress site for 2 months, controls a plugin with 200,000 plus active installs and has posted no information about themselves! To new plugin developers, trust is a very important factor when creating free plugins, add some information about yourself so your users can check you out. We now know why he didn’t post any information, he’s a hacker and bought the plugin to add malicious code to 200,000+ WordPress sites!!!
In June 2017 the new developer released an update (version 2.6.0) of the Display Widgets plugin and it’s version 2.6.* of the plugin I’ll be reviewing (nothing major wrong with the old v2.05 code).
Display Widgets Plugin Version 2.6.0 Review
The new developer rewrote the code to update the general code, unfortunately the new code broke (added a new bug) one of the basic Display Widget features: when visiting “Appearance” > “Widgets” the Display Widgets options are supposed to load when viewing a widget, with version 2.6.0 you had to click the “Save” widget button for the display widget options to show!
Version 2.6.0 didn’t appear to fix any of the (small) bugs present in v2.05 and didn’t extend any of the core widget logic features.
What it added was an automated download of another plugin (a geolocation widget: was over 50MB in size!) from a private server!
Automatically installing code from a private server is against the WordPress plugin repository rules.
The new code also connected to another server to track visitors data including:
IP Address (can potentially track you to your street address)
Webpage Visited (URL of the webpages a visitor visited)
Site URL (the URL of the WordPress site the Display Widgets plugin is installed on)
User Agent (which browser the visitors uses etc…)
Automatically tracking user data etc… without the permission of the site owner is against the WordPress plugin repository rules.
I reported the infringements to the plugin repository, simply email them via plugins@wordpress.org and explain what’s you think is wrong. I sent the WP Plugin Team over a dozen emails between June 2017 and September 2017 regarding the Display Widgets plugin.
Version 2.6.0 was removed from the plugin repository. If you are using version 2.6.0 of the Display Widgets Plugin on your site, remove it NOW.
The plugin repository are very understanding, a week or so later the developer released a new version (v2.6.1).
Display Widgets Plugin Version 2.6.1 Review
The new developer reverted back to the old v2.05 base code fixing the bug mentioned above (having to click “Save” to see the options).
Still no 2.05 bug fixes, still no core widget logic features extended.
The automated download of the 50MB geolocation plugin was removed.
Version 2.6.1 was still tracking user data without permission (see v2.6.0 review above), though he’d changed which server was connected to (no idea why, still tracked the same data???).
I reported the infringements to the WordPress plugin repository, version 2.6.1 was removed from the plugin repository. If you are using version 2.6.1 of the Display Widgets Plugin on your site, remove it NOW.
The plugin repository are very, very :-) understanding, the developer released a new version (v2.6.2).
Display Widgets Plugin Version 2.6.2 Review
Version 2.6.2 is pretty much v2.6.1 with an option to tick to turn on the tracking and a privacy notification.
The above is all that’s required for a plugin developer to track your visitors data: basically click an option to turn a feature on and inform the site owner “I’m tracking your user data”. I contacted the plugin repository and they confirmed the above is all that’s needed: it’s not up to the plugin repository what WordPress site owners add to their sites, their rules are to make sure the site owners are informed about what they’ve installed NOT to protect them from installing bad plugins.
Anyway, slight problem with this, under EU (and other country laws) to track visitor data this way the SITE OWNER (not the plugin developer) legally has to inform their visitors their data is being tracked by a third party (the third party being the plugin developer). In practice this means if you use the Display Widgets plugin version 2.6.* you need a privacy policy (like my privacy policy) explaining a third party tracks your data: I use AdSense on this site, AdSense is a third party tracking my visitors data.
This is the content of my WordPress support forum post: https://wordpress.org/support/topic/display-widgets-plugin-geolocation-tracking-visitors-without-permission/
Display Widgets Plugin Geolocation Tracking Visitors without Permission
I have a question regarding the visitor data you are tracking/storing and your terms at http://geoip2.io/terms.html
Section 10. Privacy policy states:
We will collect website information by lawful and fair means and, where appropriate, with the knowledge or consent of the individual concerned. Before or at the time of collecting such information, we will identify the purposes for which information is being collected. We will collect and use such information solely for fulfilling those purposes specified by us and for other ancillary purposes, unless we obtain the consent of the individual concerned or as required by law. Website data should be relevant to the purposes for which it is to be used, and, to the extent necessary for those purposes, should be accurate, complete, and up-to-date. The following data is currently collected for analysis and in order to optimize GeoIP2.io’s performance:
Website and Page URL – Collected to track service usage by Country, Region and Domain; we reserve the right to blacklist certain domains that exceed reasonable service usage
Visitor’s User Agent and IP Address – Required to determine Visitor’s Country of origin
As a visitor to WordPress sites including some running the Display Widgets plugin, how are you for-filling this part of your privacy policy when I visit a site with the GeoIP2.io’s Geolocation tracking enabled:
with the knowledge or consent of the individual concerned. Before or at the time of collecting such information, we will identify the purposes for which information is being collected.
As “the individual concerned” how and when did you inform me you are collecting my user data and how did you gain my consent and how did you inform me the reason for collecting my data?
For the record you have tracked my data (check your logfile) and I didn’t receive a notification explaining any of this (no pop up or privacy policy explaining GeoIP2.io is tracking my visit).
You have my IP address (90.216.105.28), the user agent (Mozilla Firefox etc…), the webpage I connected from (one of my localhost test servers on my PC), it’s a WordPress Post (/embed-tests/) for testing WordPress embed code. You even know the folder (/str-2016-09/) on my PC I was running the test server from and that it’s running WordPress 4.8.
Example data you’ll have in your weblog:
90.216.105.28 - - [04/Jul/2017:10:46:24 -0700] "GET /api/update/?url=http%3A%2F%2Flocalhost%2Fstr-2016-09%2Fembed-tests%2F&agent=Mozilla%2F5.0+%28Windows+NT+6.1%3B+WOW64%3B+rv%3A54.0%29+Gecko%2F20100101+Firefox%2F54.0&geo=true&p=9&v=0&ip=127.0.0.1&siteurl=http%3A%2F%2Flocalhost%2Fstr-2016-09 HTTP/1.1" 403 3 "http://geoip2.io/api/update/?url=http%3A%2F%2Flocalhost%2Fstr-2016-09%2Fembed-tests%2F&agent=Mozilla%2F5.0+%28Windows+NT+6.1%3B+WOW64%3B+rv%3A54.0%29+Gecko%2F20100101+Firefox%2F54.0&geo=true&p=9&v=0&ip=127.0.0.1&siteurl=http%3A%2F%2Flocalhost%2Fstr-2016-09" "WordPress/4.8; http://localhost/str-2016-09"
I got the example by changing the GeoIP2.io URL (in the geolocation.php file) to one of my domains and checked it’s logs. You will have almost identical entries in your weblogs (only difference will be the time I connected).
Your terms also state:
“We will make readily available to customers information about our policies and practices relating to the management of such information.”
I guess I’m considered a customer?, please make available information about your policies and practices relating to the management of my information.
How do I gain access to the data you store about me?
I don’t want my data tracked by GeoIP2.io. How do I get you to delete the data and stop you from collecting anymore of my data? Note I’m with an ISP with dynamic IPs: my IP changes every time the router is turned off/on.
Can I suggest you do some serious research regarding privacy laws.
David
Take into account the new developer at the time of my forum post above hadn’t supplied any other way to contact him. At the time I didn’t even know if the developer was male/female (near the end of thread he posted an email address with the name Kevin).
The WordPress support forum was the ONLY point of contact for support regarding the Display Widgets plugin and I was a plugin user asking a legitimate question regarding privacy laws.
How I Was Unfairly Moderated on the WordPress Support Forum
I did NOT receive a satisfactory response from the developer, but was warned by a WordPress support forum moderator to basically stop asking questions!
Multiple threads related to the Display Widgets plugin were (and still are) closed and some of my replies were deleted!
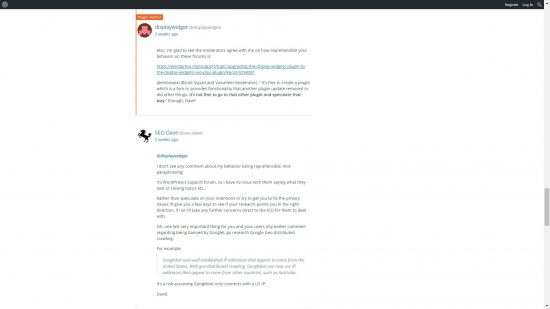
The Display Widgets Plugin developer took this as some sort of win and gloated, I responded (see screenshot below).
About 4-5 days later my forum posts were unfairly moderated for that response. I’m shocked that one response (that was my ONLY response AFTER the moderator warning) was enough to be moderated, seriously!!!
Since I was unfairly moderated I removed my four WordPress plugins from the plugin repository (my online reputation is important, and this is an insult) and decided I will no longer inform the plugin repository of other plugin developers breaking the WordPress plugin repository rules: this wasn’t my first time, I’ve reported multiple problem plugins.
If any of the WordPress support forum moderators want to defend their actions, the comments are open and I rarely moderate users :-)
Display Widgets Plugin v2.6.2.* Includes Hacking Code!!!
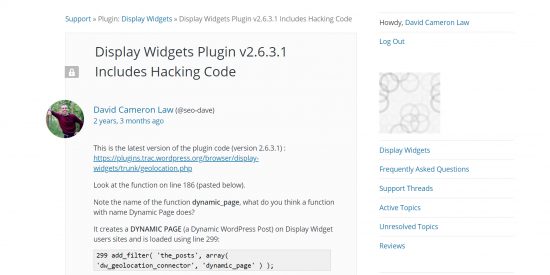
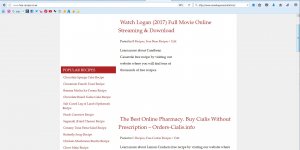
After being moderated (mid-July) I noticed another issue with the Display Widgets plugin related to code which looks like it generates a WordPress Post dynamically when logged OUT users visit a site!
Screenshot of some of the code below, it’s from the geolocation.php file:
This code allows the Display Widgets plugin developer to dynamically generate a WordPress Post on Display Widget plugin user sites (up to 200,000 sites – I think at least 50,000 updated to the 2.6.* code).
It works by first checking if the visitor is logged in, the reason for this is if the user is logged in it’s probably the WordPress site owner and a hacker doesn’t want the owner to know they are doing something malicious on the site!
If the visitor is logged in (the site owner for example) the plugin hacking code does nothing, but if the user is logged out (a normal visitor OR Google and other search engines) it connects to the plugin developers server and can grab data from the private server to create a dynamic WordPress Post with whatever content they like!
From a hacking perspective this is great, the hacker can insert SPAMMY links on a Display Widget users site to help rank the site(s) linked to, can add advertising code (AdSense for example), the dynamic content could even include ways to hack into your server to make other changes. If you’ve used any of the Display Widgets v2.6.* versions you need to do a WordPress security audit of your WordPress site (it might have been fully hacked).
Had I not been unfairly moderated on the support forum my first step would have been to email plugins@wordpress.org to inform them about the malicious code. Next step would be to post on the Display Widgets forum warning users to delete the Display Widgets plugin ASAP: for the record it’s safe to downgrade to the 2.05 version (the old version with minor bugs).
Since I was unfairly moderated, I did nothing.
Update: The Display Widgets Plugin version 2.6.2.1 (which includes the hacking code) has again been removed from the plugin repository (3rd time it’s been removed): I guess one of the thousands of hacked sites noticed and reported the issue. It will be interesting to see if the plugin repository give the new developer a third chance, I’ll be shocked if they do as this infringement is a clear case of malicious behavior (you don’t accidentally add code like this).
Display Widgets Plugin v2.6.3 Review : Still Includes Hacking Code!!!
The Display Widgets plugin has again being reinstated (v2.6.3 uploaded September 2nd 2017) and I’ve lost all faith in the WordPress plugin review team, how on Earth have they missed this malicious code AGAIN!
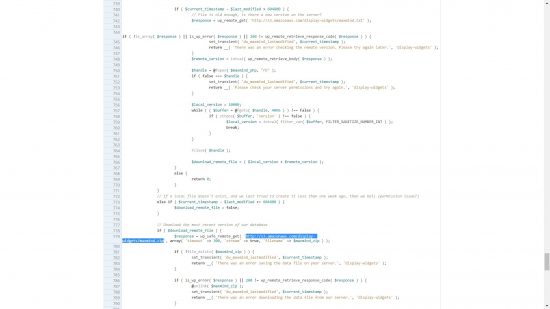
The malicious code, a serious security issue mentioned above is still within the geolocation.php file between lines 190 and 243.
Under no circumstances use this hacked plugin, if you must use the Display Widgets plugin use the 2.05 code. Download from https://downloads.wordpress.org/plugin/display-widgets.2.05.zip has a few small bugs.
I eventually got annoyed and reported the malicious code to the plugin team on the 8th September and within hours the plugin was closed permanently.
David Law




Originally posted to the WordPress support forum…
I have a question regarding the visitor data you are tracking/storing and your terms at
http://geoip2.io/terms.html: the site has been deleted.Section 10. Privacy policy states:
We will collect website information by lawful and fair means and, where appropriate, with the knowledge or consent of the individual concerned. Before or at the time of collecting such information, we will identify the purposes for which information is being collected. We will collect and use such information solely for fulfilling those purposes specified by us and for other ancillary purposes, unless we obtain the consent of the individual concerned or as required by law. Website data should be relevant to the purposes for which it is to be used, and, to the extent necessary for those purposes, should be accurate, complete, and up-to-date. The following data is currently collected for analysis and in order to optimize GeoIP2.io’s performance:
Website and Page URL – Collected to track service usage by Country, Region and Domain; we reserve the right to blacklist certain domains that exceed reasonable service usage
Visitor’s User Agent and IP Address – Required to determine Visitor’s Country of origin
As a visitor to WordPress sites including some running the Display Widgets plugin, how are you for-filling this part of your privacy policy when I visit a site with the GeoIP2.io’s Geolocation tracking enabled:
with the knowledge or consent of the individual concerned. Before or at the time of collecting such information, we will identify the purposes for which information is being collected.
As “the individual concerned” how and when did you inform me you are collecting my user data and how did you gain my consent and how did you inform me the reason for collecting my data?
For the record you have tracked my data (check your logfile) and I didn’t receive a notification explaining any of this (no pop up or privacy policy explaining GeoIP2.io is tracking my visit).
You have my IP address (90.216.105.28), the user agent (Mozilla Firefox etc…), the webpage I connected from (one of my localhost test servers on my PC), it’s a WordPress Post (/embed-tests/) for testing WordPress embed code. You even know the folder (/str-2016-09/) on my PC I was running the test server from and that it’s running WordPress 4.8.
Example data you’ll have in your weblog:
90.216.105.28 - - [04/Jul/2017:10:46:24 -0700] "GET /api/update/?url=http%3A%2F%2Flocalhost%2Fstr-2016-09%2Fembed-tests%2F&agent=Mozilla%2F5.0+%28Windows+NT+6.1%3B+WOW64%3B+rv%3A54.0%29+Gecko%2F20100101+Firefox%2F54.0&geo=true&p=9&v=0&ip=127.0.0.1&siteurl=http%3A%2F%2Flocalhost%2Fstr-2016-09 HTTP/1.1" 403 3 "http://geoip2.io/api/update/?url=http%3A%2F%2Flocalhost%2Fstr-2016-09%2Fembed-tests%2F&agent=Mozilla%2F5.0+%28Windows+NT+6.1%3B+WOW64%3B+rv%3A54.0%29+Gecko%2F20100101+Firefox%2F54.0&geo=true&p=9&v=0&ip=127.0.0.1&siteurl=http%3A%2F%2Flocalhost%2Fstr-2016-09" "WordPress/4.8; http://localhost/str-2016-09"I got the example by changing the GeoIP2.io URL (in the geolocation.php file) to one of my domains and checked it’s logs. You will have almost identical entries in your weblogs (only difference will be the time I connected).
Your terms also state:
“We will make readily available to customers information about our policies and practices relating to the management of such information.”
I guess I’m considered a customer?, please make available information about your policies and practices relating to the management of my information.
How do I gain access to the data you store about me?
I don’t want my data tracked by GeoIP2.io. How do I get you to delete the data and stop you from collecting anymore of my data? Note I’m with an ISP with dynamic IPs: my IP changes every time the router is turned off/on.
Can I suggest you do some serious research regarding privacy laws.
David
Update September 16th 2017 : I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin.
Originally posted to the WordPress support forum…
WordPress has deleted the Display Widgets plugin again, (twice in a week!) this time because of version 2.6.1.
The cause is the code in the /display-widgets/geolocation.php file (added by the new developer) connects to http://geoip2.io/ and potentially collects/stores your website visitors data without yours/theirs permission.
Data collected:
IP address
User agent
Display Widget users domain name
I don’t understand why the feature would require anything beyond IP address? The new geolocation feature only needs the country code (US, EN-GB, DE etc…) of the visitor which can be determined from IP alone. Why gather the other data?
If you plan to stick with the Display Widgets plugin I suggest downgrading to the old version (updated 2+ years ago by the original developer). You can download version 2.05 from https://downloads.wordpress.org/plugin/display-widgets.2.05.zip this has a few minor bugs, but is a stable release and what I used to build the Display Widgets SEO Plus plugin from 7 months ago.
David
Update September 16th 2017 : I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin.
I said I wasn’t going to waste my time contacting the WordPress plugin team again, but I couldn’t help myself, the Display Widgets plugin developer is a hacker and is up to no good.
It’s been a week since WordPress reinstated the Display Widgets plugin again (is that three or four times, I’m loosing track?) and they keep missing the malicious code, it’s still there!
The plugin developer pushed out a new update, v2.6.3.1 it still has the hacking code and now some base64 code (a way of hiding code: doesn’t mean it’s malicious).
My email to plugins@wordpress.org: this is the email address to report problem plugins, if your site is hacked because of the Display Widgets plugin send them an email and complain.
And I was the one moderated on the WordPress forums for asking questions about what the developer was up to!
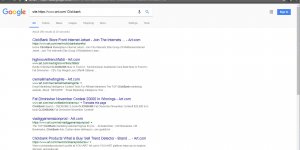
To check if your site is hacked, log out of WordPress and browse through your site for Posts that shouldn’t be there. You could also do a Google site search, simply paste
site:http://example.comInto a Google search replacing example.com with your domain name and check what Google has indexed, if you find PayDay loan Posts or similar SPAMMY posts, you’ve been hacked.
David Law
Update September 16th 2017 : I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin.
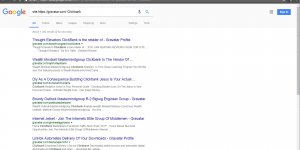
Google webmaster tools says my site is hacked by the display widget plugin, its filled with spam links to pay-day loan companies when not logged in!!!
how do i remove the spammy links and secure my site???
I would like to try your plus version but its gone! would the plus version remove the spam links ands secure WordPress???
WordPress should give you the display widgets plugin and you should post your plus version in its place with the extra options
please help!!!
Jackson
Sorry to hear your site is hacked, there’s probably tens of thousands of Display Widget v2.6.* users in the same boat!
I’ve not looked at a Display Widget Plugin v2.6.* hacked site, so not sure how much WordPress security damage it does. If it’s a simple case of the dynamic Post hacking code just adds a dynamic Post and does nothing else it will be easy to fix.
Remove v2.6.* of the Display Widgets Plugin and it’s fixed.
The problem is with the option to add a dynamic Post means the Display Widget Plugin developer (@displaywidget) could insert other malicious code via the dynamic Post. If the hackers done this there could be backdoors added to the site and that’s a much bigger WordPress security issue: you have to find them to secure the site.
First step is remove the Display Widgets Plugin v2.6.* and check if deleting the plugin fixes the spammy links when a user is logged out.
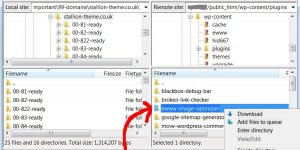
You can delete the plugin in two says, use an FTP program and manually delete the /display-widget/ plugin folder (under /wp-content/plugins/display-widgets/). Or under the Plugins menu click the Delete link associated with the plugin.
That should remove the dynamic Post with the spammy links (check when logged out). To be safe I’d at least update the WordPress password just in case.
If it was my site first using FTP I’d download a full copy of the sites files, I’d also use my server controlpanel to make a backup of the entire site (this gives me a backup of the files and the database).
I’d then look through every directory for anything out of place (looking at file dates can help) and even if I didn’t find anything reinstall WordPress manually via FTP deleting old files and replacing with new.
Basically I’d get the latest WordPress zip file, extract it on my PC, rename the folders within:
Rename: /wp-admin/ to /tempwp-admin/
Rename: /wp-includes/ to /tempwp-includes/
Upload the two folders via FTP, when uploaded rename the original folder:
Rename: /wp-admin/ to /oldwp-admin/
Rename: /wp-includes/ to /oldwp-includes/
Next
Rename: /tempwp-admin/ to /wp-admin/
Rename: /tempwp-includes/ to /wp-includes/
The above gives you a clean version of the main WordPress directories.
Also upload the new files from the zip file wp-activate.php, wp-blog-header.php etc… (there’s around 16 files) over the old and manually check what files are unchanged (some old installs have out of date WordPress files, delete them) in the root of the WordPress install: (.htaccess, wp-config.php for example won’t be over wrote DO NOT delete them), you should download these files and manually check them for changes.
The above will give you a clean install of WordPress, if the site works delete the old folders /oldpwp-admin/ and /oldwp-includes/.
Next is check what’s in the /wp-content/ directory, this is usually where images, plugins, themes and caches are stored. Delete all plugins you don’t use (if it isn’t active, delete it), delete all themes you don’t use keeping one of the default WordPress themes like TwentySeventeen (should have no more than three themes in the themes folder: one default theme, one parent theme, one child theme). Exception to this is if you are on a multi-site version of WordPress and different sites use different themes: same concept, but keep all active themes.
Like what I did with the /wp-admin/ folder I’d do similar for the /plugins/ and /themes/ folders. On my PC I’d create two folders /tempplugins/ and /tempthemes/ and put in them fresh copies of the plugins and themes I use. I’d upload them to the /wp-content/ folder and then rename /plugins/ to /oldplugins/ and /themes/ to /oldthemes/ (when everything is working delete the /oldfolders/.
This way I get a clean version of most of WordPress, other folders under /wp-content/ I’d check manually, if a cache plugin was installed I’d clear the cache (should delete a lot of the cache files) and manually check what’s left.
By doing the above if a hacker has uploaded a backdoor script to any of the directories you’ve replaced they are gone for good. You just have to be careful manually checking what’s in the wp-config.php file the .htccess file and anything under /wp-content/ you didn’t delete/replace.
You also have to check below your root directory. On my server the root directory is under /public_html/, but below that folder is /awstats/, /cgi-bin/, /tmp/ etc… these all need checking manually. On my system /tmp/ for example should be empty, but sometimes old session files remain, I delete them all.
After that I’d check through the database for changes and look through the site when both logged in and logged out for anything untoward. I’d also change all passwords, that includes the passwords for FTP access to the server, the MySQL password (update the wp-config.php file) and the WordPress login password.
There is no right way to do this (I prefer the manual approach as I won’t miss anything: a security script could miss something), it’s a case of looking for things that shouldn’t be there and as every site is different…
All that being said, when I’ve been hacked (I’ve owned 100s of domains it’s impossible to be 100% secure for 15+ years) I’ve always reverted back to the last clean backup, change the passwords just to be safe and make sure whatever was vulnerable is fixed: regular backups are your best friend :-)
David Law
Update September 16th 2017 : I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin.
Dave
Re: “How to Clean a Hacked WordPress Site (September 11th, 2017 at 16:24)”
Your comment is the best description of how to clean a hacked website that I’ve seen. It deserves to be in an article of its own somewhere and I’m pretty sure it would be generating traffic for years to come…
I’m here looking to fix a website trashed by the Display Widgets plugin. I had weekly backups going back 5 weeks which wasn’t enough so I’m being forced to do it manually :(
I’ll add my thanks for the work you have put in to helping expose and fix the malicious code in the plugin and my vote that your ‘moderation’ in the WP forums be reversed.
David,
Thanks for the information. It is very helpful I have a number of sites using Display Widget and I’m quite concerned about the damage it can cause.
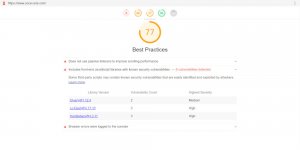
I use WordFence and it showed that version 2.6.3 needed to be updated to v2.7. I haven’t yet found any information about a version 2.7. Have you seen anything?
Is it possible to simply comment out or delete the malicious code from version 2.6.3? That seems like it could be the most expedient route.
Your thoughts?
Clay
There’s some info on the Display Widgets support forum about the 2.7 update, but you can’t get to it easily because the main Display Widget Plugin page is still closed (weird way to fix this issue if you ask me).
These are direct links to:
The Display Widget support forum: https://wordpress.org/support/plugin/display-widgets/
Specific thread about v2.7: https://wordpress.org/support/topic/display-widgets-2-7-is-safe/
Direct link to v2.05 zip: https://downloads.wordpress.org/plugin/display-widgets.2.05.zip
Direct link to v2.7 zip: https://downloads.wordpress.org/plugin/display-widgets.2.7.zip
The 2.7 zip file is pretty much identical to v2.05: updated about 3 years ago: has a few minor bugs, but no security/privacy issues.
If you have any version installed (other than my v3.0.0) there should be an update available under your Dashboard.
Direct link to my v3.0.0 zip: https://seo-gold.com/
My v3.0.0 code is v2.05/v2.7 with some of the minor bugs fixed and a small feature update (can hide widget titles on the front end).
Since the WordPress plugin team say the Display Widgets plugin is closed for good it doesn’t make much difference which version you use as long as it’s v2.05, v2.7 or v3.0.0. Do NOT use v2.6.*. There won’t ever be another update available on the plugin repository, unless the plugin team change their mind and a new developer takes over development.
So it’s a case of install v2.05, v2.7 or v3.0.0 and forget about it: the plugin is relatively straight forward code, highly unlikely to stop working in the medium term: should be good for 5+ years he says looking to 2022 when I’ll eat my prediction :-)
Yes, you could clean v2.6.3.1, but the end result would be v2.05. The new developer (who is now banned from the WordPress site) didn’t add any new useful features or fix the bugs to the core 2.05 plugin. He took v2.05 code and added a tracking feature (the developer could track your visitors: not much use to you) and added a way to hack your site.
Easier (and safer) to use v2.05, v2.7 or v3.0.0.
David Law
Update September 16th 2017 : I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin.
Very long-term Display Widget users here, we’ve been running the plugin on a fifty+ domain PBN.
I found my way to your site through Wordfence https://www.wordfence.com/blog/2017/09/display-widgets-malware/. You were instrumental in protecting WordPress users from a despicable low-life hacker, without your multiple interventions we would still be running vulnerable code!
We’ve performed a full security audit securing the network.
And your reward for helping the community, the WP-plugin team moderates your support threads and closed your forked plugin!
The WP-plugin team should be ashamed of their behaviour.
On behalf of the WP community, thank you for your hard work.
I completely agree with Jackson, the Display Widgets plugin shouldn’t be closed, you should adopt the plugin. Have you asked the WP-plugin team about adopting?
Nathan G
Thanks for your kind words :-)
A couple of small inaccuracies in your comment above.
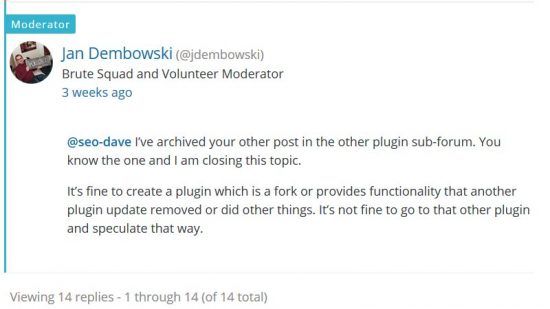
The WordPress plugin team didn’t delete/close/moderate my WordPress forum support posts, it was “Jan Dembowsi” (@jdembowsi) a member of the “Brute Squad and Volunteer Moderator” team. Guess you’d call them the moderator team?
The WordPress plugin team didn’t close my forked Display Widgets SEO Plus plugin, that was my decision, I asked them to close it (there’s nothing wrong with the forked plugin).
When I discovered the moderation lock on my WordPress account I couldn’t offer instant support to my plugin users (I had four SEO plugins in the repository and planned a dozen more). The moderation lock said it could take up to 72hrs for a moderator to check and approve my contributions and I can’t offer support with a delay of up to 3 days!
I’ve been a member of the WordPress support site for over 10 years without any issues, I’ve reported multiple plugin issues (direct to the plugin team via plugins@wordpress.org) and reported core bugs etc…
Being unfairly moderated is an insult and a mark on my reputation and two of the WordPress plugin team (Mika and Otto) I’ve discussed this with (via email) believe I deserved the moderation lock!
I can not support a system which has what I think is an entrenched view: the moderators are always right, everyone else is wrong.
Regarding adopting the Display Widgets plugin…
I’d be the perfect developer to adopt the Display Widgets plugin, I’ve been working with the plugin code for over 5 years and have forked the code into a much better version: Display Widgets SEO Plus.
The forked version is an upgrade to the Display Widgets plugin v2.05/v2.7 fixes all the 2.05/2.7 code bugs, covers pretty much all default widget logic options (v2.05/v2.7 has basic logic options), fixes the WPML language plugin support (it’s broken in v2.05/v2.7) and adds new logic support for the bbPress plugin and the BuddyPress plugin (was going to add Woocommerce logic next).
A few months back I offered to adopt the Display Widgets plugin, but because the new developer had bought the plugin it appeared to be not an option.
After being moderated the only way I’d consider adding my SEO plugins back on the plugin repository or taking responsibility for the Display Widgets plugin (it’s got 200,000+ active installs, that’s potentially a lot of support to deal with) is after receiving an apology for being moderated.
I’m never going to get an apology (not asking for one), so it’s not going to happen.
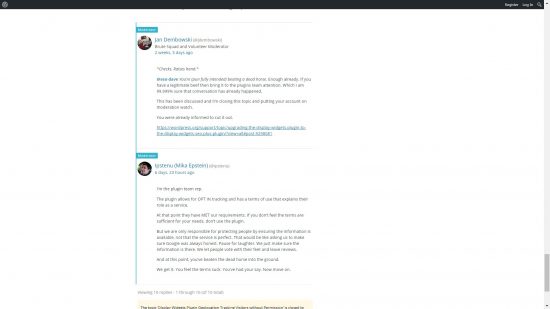
For the record I accepted the moderator warning (even though that was unwarranted IMHO) https://wordpress.org/support/topic/display-widgets-plugin-geolocation-tracking-visitors-without-permission/#post-9307142 : that was a warning to basically stop asking questions about the intentions of the @displaywidget developer, you know the developer who was tracking Display Widget plugin users sites traffic without permission and adding malicious code to tens of thousands of WordPress sites!
My problem is with being actually moderated for this single short comment: https://wordpress.org/support/topic/display-widgets-plugin-geolocation-tracking-visitors-without-permission/#post-9298901
If this comment is enough to be moderated, how can anyone work within their draconian moderation rules?
That was my final (only) comment after the moderation warning.
A few days after making the above comment I was moderated, I made no further posts in the Display Widgets forum until September (months later), so it must be that one comment which got me moderated.
My next contribution was about a week later supporting one of my plugin users at https://wordpress.org/support/topic/widget-not-showing-at-first-page-of-all-search-results/#post-9317899 which is when I discovered the moderation lock on my account!
I’ve asked both Mika and Otto (plugin team) what is wrong with the above comment and they both think it’s enough to be moderated!!!
If anyone can tell me what is wrong with the above comment (that was my ONLY comment after being warned by Jan Dembowsi) I’d love to know????
Funny thing is I closed all my plugins after being moderated, made four support threads (one for each plugin) like this one https://wordpress.org/support/topic/plugin-removed-from-repository-3/ to inform users I’d closed the plugins and those support threads resulted in the moderation lock being removed.
If I deserved the moderation lock why was it lifted so quickly when all my posts (after discovering the moderation lock) were complaining about being moderated?
Jan Dembowsi was wrong to moderate my account and the plugin team are wrong to defend the moderation.
It’s unfortunate there isn’t a popular alternative to the WordPress plugin repository, it’s difficult to get momentum for a plugin not in the free repository, so not much point re-releasing my SEO plugins or building new ones.
David Law
Update September 16th 2017 : I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin.
Thank you, thank you, thank you! It’s nice to no that
integrity still exists in a world that no longer values
it. Great job SEO Dave! I’ve learned a lot from this
reading, and I will stay tuned.
Ron
I am just stopping by to say thank you!
I’ve been using Display Widgets for years. Upgraded continuesly aside from the last version.
The only way I could see something was up when I click to see “details”. Then I saw the plugin had been deleted. I figured something was wrong. Googles, got to wordfence then your site.
WP Plugin team have a real issue here. Merely deleting the plugin form the repository will do nothing for anyone currently with it. Only make the spam worse. A simple warning text when trying to updated it would do – I don’t think it’s complicated.
Next, thank you very much for your hard work in bringing this to fruition.
I deleted the plugin. Reinstalled version 2.5. Is that enough to ensure any malicious code has been removed?
I plan to switch over to another plugin once I know the above
I’ve released a Free Security Update/Upgrade of the Display Widgets Plugin which is called v4.0.0 and is malicious code free and extends the widget logic features. I’ll be supporting the new version with new future updates: it’s not going in the WordPress Repository so I’ve added a custom update library (updates from my server not the WordPress plugin repository).
I couldn’t agree more about the plugin team having a real issue here, the Display Widgets plugin has really highlighted failings in their system, a system best described as putting out fires rather than fire prevention: I emailed them over a dozen times about this plugin and they missed the malicious code at least twice when they rechecked the code!!!
The Display Widgets plugin isn’t even a big plugin, the hacked versions were two files, one containing pretty much the original 2.05 code and the geolocation.php file that was 50% tracking code and 50% malicious code (to create a dynamic post to hack sites). I’d hate to think what could be hidden in some of the huge plugins (dozens of php files) in the repository!
I’m just a WordPress user like you and noticed the tracking issue, but wasn’t looking for malicious code, the plugin team should be looking for this sort of thing when a new developer with no track record has consistently broken the plugin repository rules over and over again with a plugin they paid money for: that should have rang alarm bells, a business doesn’t buy a plugin without a plan to monetize and free plugins are difficult to make money from.
This is a case study of incompetence, they missed the malicious code at least twice, missed user reports (including a trac ticket) of malicious code, took days to release the v2.7 update and still haven’t forced a upgrade meaning there’s tens of thousands of WordPress sites running vulnerable 2.6 code which THEY are responsible for allowing in the repository!
Regarding hacked sites, I wrote a comment about how to clean a site at How to Clean a Hacked WordPress Site.
I’m still not sure how much damage the hacker has done to WordPress sites, so don’t know how much to worry about this.
David Law
Hi Dave, great work on spotting the issues with the original plugin, I was actually unable to update from within WordPress which lead me here, i had already started migrating sites to your version before all this happened. I now find myself wondering what to do as you have removed your version, I understand your reasoning why but I think now is the time everyone needs to migrate over to your plugin and for that to happen it needs to be on the repository.
For the sake of us WordPress users i hope you reinstate the plugin. For now I have just downloaded the latest version of your SEO version 3.0 from the repository (I’ts still on there: https://downloads.wordpress.org/plugin/display-widgets-seo-plus.3.0.0.zip) and will update any sites running the standard version to this. i like many other hope you carry on working on the plugin and hope to see it back on the main repository soon as there is no good alternative.
Thanks for all your hard work.
Hi,
i have installed version 4.0
But after delete or update the hacked version i have problems with login (cookie problem) and other actions like a white site after save a site and many more.
Is there anything else, what the hacked version changed?
Sorry to hear of the problems.
In principle yes the hack could have compromised your site in other ways.
I never installed the Display Widgets Plugin v2.6.* on a live site, only tested it in Localhost, so have no examples to look at beyond the “displaywidgets_ids” example I’ve pasted below (that was from my localhost test install).
The Display Widgets plugin v2.6.* adds a database option in the “wp_options” table looks like this:
displaywidgets_ids
a:1:{s:26:"__3371_last_checked_3771__";s:10:"1499359495";}
This in itself doesn’t cause any harm per se, but the entry and the plugin code allowed the developer to add a dynamic post into your database.
I don’t have an example of what this looks like, but understand it includes the name of the plugin “Display Widgets” and would assume it’s also in the “wp_options” table.
I’m afraid it’s a case of going through the database to see if anything stands out, for most WordPress sites the wp_options table tends to be below a few hundred entries so doesn’t take too long to look through. You are looking for anything that mentions Display Widgets or displaywidgets.
If the hacker went as far as to add one of these dynamic posts into your database there’s no reason why the entry couldn’t include other malicious code.
So basically they add a database entry which the malicious plugin (v2.6.*) uses to make a dynamic post database entry, but it could also be used to do other malicious things to your site. They could add all sorts of vulnerabilities to add backdoors.
The best advice would be to use a backup from before you installed the v2.6.* code, but that could be a backup from over 3 months ago!!!
Even though I have regular backups, if I had installed the malicious code I couldn’t go back three months (would loose important articles/comments), so would have to go with a manual security clean. I wrote a comment about what I’d do with the sites files at How to Clean a Hacked WordPress Site.
Now I know a little more about what the backdoor hack does I’d also go through the database looking for options related to displaywidgets (did this in my localhost test installs, found nothing).
The person/people behind the malicious code has been doing this for years, they own loads of sites related to payday loans, finance, gambling… and have been hacking sites for years (found one mentioned on the WP forums from ~4 years ago) to add SEO link SPAM (they have a very well thought out SEO link SPAM program: I’m impressed). To put things into perspective the main suspect is in his early twenties and lives in a property that was bought in December 2016 for over £750,000 and they say black hat SEO techniques don’t work anymore :-)
BTW Before doing anything I’d look through your sites log files for errors, white screen suggests a 500 error. The logs can point you in the right direction.
If you find it difficult to access your log files you can also get WordPress to output a “debug.log” file by adding this to your “wp-config.php” file:
Download the “wp-config.php” file via FTP to your computer, edit it with a text editor.
Find this line:
$table_prefix = 'wp_';Might not be ‘wp_’, doesn’t matter.
Below it add
define('WP_DEBUG', true);define('WP_DEBUG_LOG', true);
define('WP_DEBUG_DISPLAY', false);
when there’s errors it creates a file under:
“example.come/wp-content/debug.log” this file is publicly available (anyone can read it).
Browse through your site and check the file (can load it in a browser).
After finding and fixing the errors modify the code to:
#define('WP_DEBUG', true);#define('WP_DEBUG_LOG', true);
#define('WP_DEBUG_DISPLAY', false);
Adding # comments out the code so it won’t run, but it’s in the file for next time (just remove the #s to check for other issues).
Also go to “/wp-content/” and delete the “debug.log” file, error notifications can be used by hackers to test for vulnerabilities, so you don’t want an easy to find log file left behind.
If you want to harden WordPress a little also add this to the “wp-config.php” file:
# Disable Editing in Dashboarddefine('DISALLOW_FILE_EDIT', true);
This turns file editing under your Dashboard off: this assumes you don’t edit plugin and theme files under your Dashboard (which you shouldn’t do as there’s no backup).
David Law
I cannot say enough how grateful I am for your research and detailed explanation. WordPress seriously needs to re-evaluate how they deal with abandoned plugins and problem plugins like this. At this point, we don’t know if a plugin just doesn’t have an update or was abandoned without researching each an every one regularly. Thank you again!