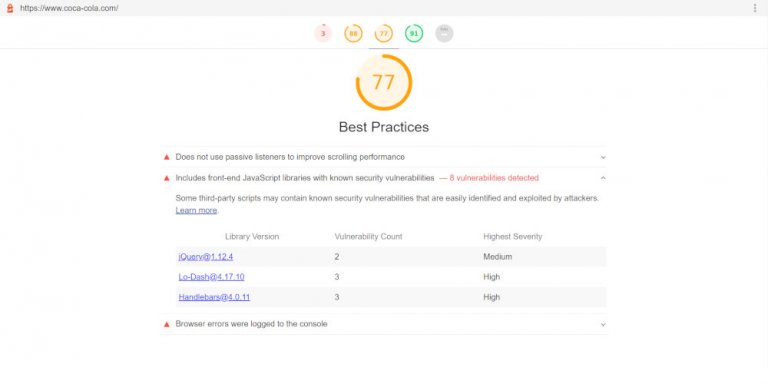
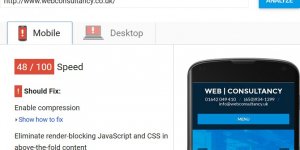
The screenshot is from a Google Lighthouse test of the Coca-Cola homepage.
At the time of the Lighthouse test (May, 2020) the Coca-Cola homepage gave the Includes front-end JavaScript libraries with known security vulnerabilities warning due to old versions of three JavaScript libraries:
- jQuery v1.12.4
- LoDash v4.17.10
- Handlebars v4.0.11
From a few Google searches, here’s a list of possible LoDash v4.17.10 cyber security vulnerabilities.
LoDash v4.17.10
Affected versions of this package are vulnerable to Prototype Pollution. The function defaultsDeep could be tricked into adding or modifying properties of Object.prototype using a constructor payload.
Affected versions of this package are vulnerable to Prototype Pollution. The functions merge, mergeWith, and defaultsDeep could be tricked into adding or modifying properties of Object.prototype. This is due to an incomplete fix to CVE-2018-3721.
Affected versions of this package are vulnerable to Prototype Pollution. The function zipObjectDeep can be tricked into adding or modifying properties of the Object prototype. These properties will be present on all objects.
Affected versions of this package are vulnerable to Regular Expression Denial of Service (ReDoS). It parses dates using regex strings, which may cause a slowdown of 2 seconds per 50k characters.
The solution is upgrade the jQuery, LoDash and Handlebars scripts to the latest version.
Continue Reading Includes front-end JavaScript libraries with known security vulnerabilities