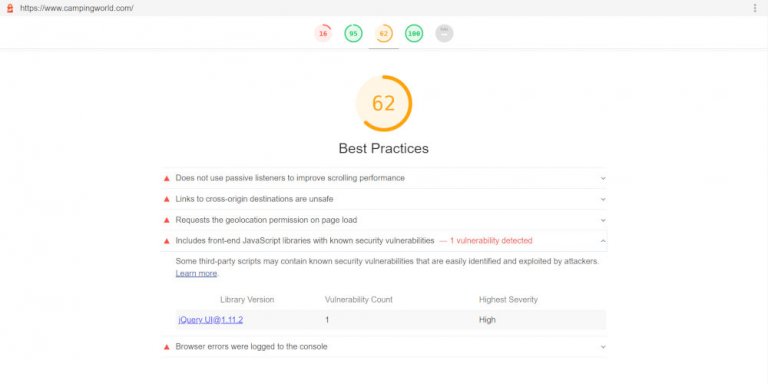
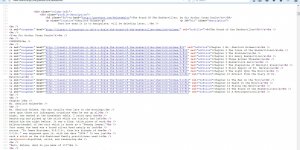
The screenshot is from a Google Lighthouse test of the Camping World homepage.
At the time of the Lighthouse test (May, 2020) the Camping World homepage gave the Includes front-end JavaScript libraries with known security vulnerabilities warning due to an old version of the jQuery UI 1.11.2 script.
From a few Google searches, here’s a list of possible cyber security vulnerabilities.
Cross-site scripting (XSS) vulnerability in jQuery UI before 1.12.0 might allow remote attackers to inject arbitrary web script or HTML via the closeText parameter of the dialog function.
Affected versions of this package are vulnerable to Cross-site Scripting (XSS). Passing HTML from untrusted sources – even after sanitizing it – to one of jQuery’s DOM manipulation methods (i.e. .html(), .append(), and others) may execute untrusted code.
Affected versions of this package are vulnerable to Cross-site Scripting (XSS) attacks when a cross-domain ajax request is performed without the dataType option causing text/javascript responses to be executed.
Affected versions of this package are vulnerable to Prototype Pollution. The extend function can be tricked into modifying the prototype of Object when the attacker controls part of the structure passed to this function. This can let an attacker add or modify an existing property that will then exist on all objects.
The solution is upgrade the jQuery script to the latest version.
Continue Reading Includes front-end JavaScript libraries with known security vulnerabilities