Earlier this year an SEO link SPAMMER paid $15,000 for access to a very popular WordPress plugin with over 200,000 active installs, see my Display Widgets Plugin Review.
The SEO link SPAMMER added malicious code to the Display Widgets plugin v2.6.* which gave them a backdoor into a WordPress sites database, basically the backdoor was used to create a dynamic Post on the websites with SEO link SPAM to payday loan companies etc…
Even though I posted about the malicious code (see link above) way back in mid-July (and another WordPress user also posted a WordPress trac ticket a few days after I wrote the above review), it took over a dozen emails to WordPress to finally get WordPress to remove the malicious code from the plugin repository on September 8th 2017!
Unfortunately WordPress has been inept/incompetent in this matter and still haven’t pushed out a forced update to protect the tens of thousands of WordPress users they failed to protect.
I estimate 50,000 WordPress sites updated to the malicious Display Widgets plugin code before it was finally removed from the WordPress plugin repository in September!!! This will cost site owners their SEO rankings as Google finds the hacked sites and downgrades them! Every minute counts with cyber security, had WordPress forced out an upgrade on September 8th/9th (I sent them an updated file to use, they didn’t want it!) it would have protected some sites from being compromised. I’ve since released a Display Widgets Plugin Security Update and as you can see in the comments users are still being hacked!
Blackhat SEO Link SPAMMING
I’ve been working in SEO for over 15 years and have to admit my first steps into SEO (around the year 2000/2001) relied heavily on black hat SEO link spamming techniques: nothing illegal- guestbook, forum and comment link SPAM which worked really well back then. I stopped using black hat SEO link building techniques after my most important site was banned by Google (in 2001), but still try to keep up with the latest black hat SEO techniques.
Last couple of days I’ve been researching cyber security and SEO link SPAM (not looked into it in great detail before) and found some interesting examples of hacked/compromised sites with SPAMMY SEO links.
A particularly good find is at least 300 webpages added to art.com which links out to Clickbank affiliate products: the links were live on September 23rd and based on research have been live since at least early July (over 2 months ago!) as I write this article.
Art.com Compromised with Clickbank Affiliate Link SPAM
Art.com is a multi-million dollar business, according to their Corporate About Page: http://corporate.art.com/aboutus/default.asp
Having served more than 19 million customers in 150 countries, Art.com Inc. is the world’s largest online specialty retailer of high-quality wall art and complementary décor. The company was founded in 1998 with one goal – to help people find the art they love so they can love their spaces more. We’ve since increased our assortment to more than 2 million images and expanded who we serve to include national retail partners, museums, hotels, interior designers and more.
You would think they’d have decent cyber security, apparently not. This type of compromised page is relatively easy to find.
I won’t go into how I found this hack, I stumbled on a footprint black hat SEO link SPAMMERS are leaving behind and if I post it here, the smart ones will adapt making it harder to find more hacked sites.
Checking art.com for Compromised WebPages
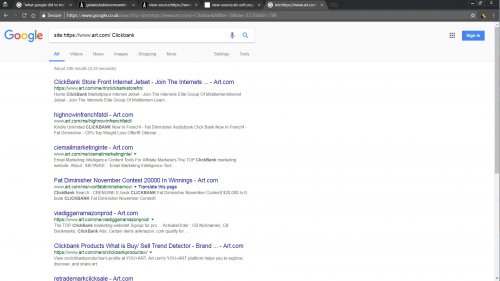
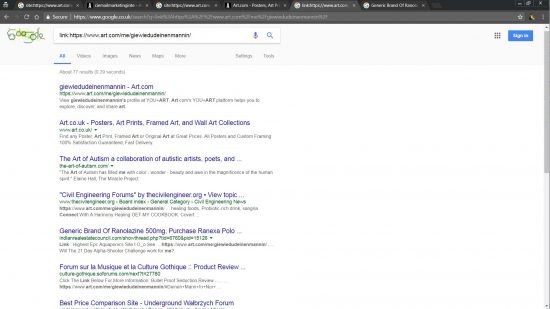
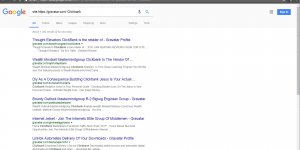
Check this Google site search: https://www.google.co.uk/search?q=site:https://www.art.com/+Clickbank
This searches the art.com site for pages with the word Clickbank, currently almost 300 pages indexed. This might not be all the compromised pages, this finds the ones that have mentioned Clickbank in the text (could be thousands more not linking to Clickbank products).
Slight SEO Tip Diversion
Anyone can perform this sort of check on their sites for obvious SEO link SPAM, searches for PayDay loans, Viagra and similar are going to stand out. For example this Google site search: https://www.google.co.uk/search?q=site:https://www.art.com/+PayDay lists 162 pages found, many of these pages are fine, but I see some comment link SPAM and one result led me to a gallery with hundreds of SPAMMY comments as far back as 2012.
The above is standard comment links SPAM added over a 5 year period, most of it will be automated and should be cleaned from the site: looks bad and Google might downgrade pages filled with SPAM.
Back to cyber security…
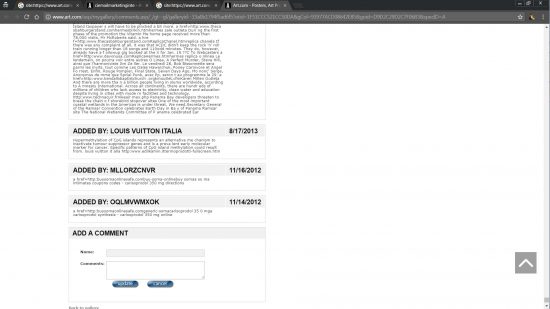
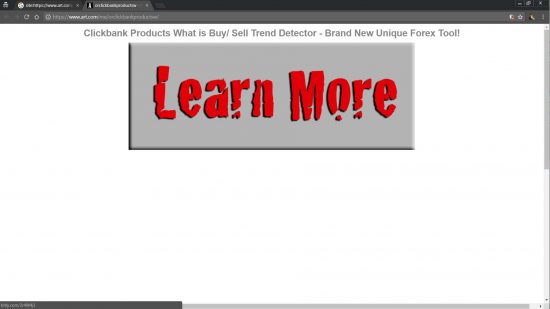
Opening the webpages with URL format: https://www.art.com/me/##########/ loads a webpage on art.com with an image link to a Clickbank affiliate product.
Clicking the links takes you to a Clickbank affiliate product: note the owner of the product is NOT responsible for these SPAMMY links, they haven’t done anything wrong. Clickbank is a legitimate business which allows products to be sold using affiliate marketing techniques. This is a Clickbank affiliate trying to make money by compromising sites like art.com with affiliate links.
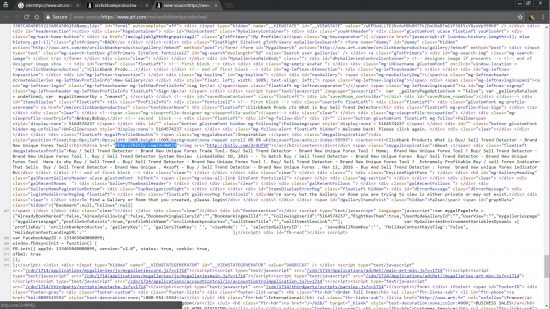
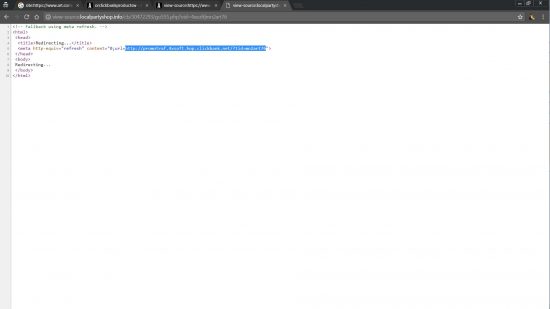
View Source of the art.com compromised page shows a bitly short URL link (a way to make shorter links, but also used to semi-hide where a link goes).
As you can see in the screenshot above of the source code the Clickbank affiliate link is semi-hidden via a bitly link, you can also see the surrounding code is the normal art.com webpage code indicating the SEO link SPAMMER hasn’t hacked the art.com site per se, (they haven’t uploaded HTML webpages) but has presumably found an exploit in their membership system which allows them to add the above affiliate link code as part of the profile or something (will be stored in the database): I’m not an art.com member so no idea how their system works. Can guess whoever wrote the code behind the membership part of the site isn’t sanitizing the uploaded data allowing HTML code to be uploaded and output as HTML code (rookie mistake).
To track this further let’s see where the bitly link goes, take a bitly link htp://bitly.com/2r4W4j1, and add view-source: like this view-source:htp://bitly.com/2r4W4j1 and load that in a browser (Firefox/Chrome) to see where the link redirects to:
From this we have two important URLs, in the top browser bar a site that’s either owned or controlled (could be a hacked site) by the SEO link SPAMMER and where that page redirects to, which is a Clickbank affiliate Hop link.
From the Clickbank Hop link we can pull the Clickbank username: promotraf
The owner of the Clickbank account ‘promotraf‘ is our SEO link SPAMMER and Clickbank presumably have the contact details and bank account details of our bad guy.
If you look through the compromised art.com pages and check the various bitly links you will find they redirect through multiple domains, but all the ones I tested used the same Clickbank account ‘promotraf‘.
Looks like we have a prolific SEO link SPAMMER with a lot of sites.
SEO Promotion of Compromised Art.com WebPages
The link SPAMMER didn’t stop here, not much value having these pages on art.com without Google indexing and ranking them, so the link SPAMMER has been SPAMMING forums etc… with links to the art.com compromised webpages: they wouldn’t be indexed and potentially ranked in Google otherwise.
Indicates the link SPAMMER knows what they are doing SEO wise, a less sophisticated attack would stop at adding the compromised pages to art.com and hope Google would find them via the art.com membership system.
Going to the forums with the link SPAM (check the Googlecache, the forum owners delete most of it quickly) not only shows the links to the compromised webpages on art.com, but many other websites!
With minimal effort I’ve potentially tracked dozens of sites which have been hacked/compromised by the SEO link SPAMMER who owns the Clickbank account ‘promotraf‘.
David Law





This is funny.
As you can read in the main article I tracked an SEO link SPAMMERS Clickbank account name: promotraf
Do a Google search for: promotraf and the first result is a Clickbank Hop Link (an affiliate link) with the promotraf username and it links to a site offering a “CriminalAudit – Background Check Service”.
Now that’s funny, a cyber criminal is promoting a background check service with illegal hacking techniques :-)
The site offers the following criminal checks:
Criminal, Arrest, Felonies, Misdemeanors, OUIs, DUIs, Sex Offender Records, Incarcerations, Public Records, Court Records
For the record this site hasn’t done anything wrong, they are promoting their service via Clickbank and the link SPAMMER has linked to them with affiliate links.
David Law
I published the Cyber Security and SEO Link SPAM article on the 23rd September 2017 (over 2 weeks ago), right after publishing I emailed art.com’s corporate email address to let them know they have a serious blackhat SEO link SPAM issue.
Tweet Image
To date I’ve received no response and the compromised webpages are still online!
There are several things wrong here.
1. Art.com corporate either hasn’t passed on the relevant information to the relevant person/people to deal with this or they have and it’s being ignored.
2. The people/person responsible for cyber security isn’t keeping track of relevant Google SERPs/Tweets on Twitter.
3. The people/person responsible for SEO isn’t keeping track of relevant Google SERPs/Tweets on Twitter.
4. The people/person managing art.com’s Twitter account is either not reading notifications (see below) or is, but isn’t passing on the relevant information.
For a big business you would expect at least one person to be keeping an eye on the brand (THE BIG PICTURE) on social media etc… to head off potential issues: a customer complains about something (rightly or wrongly) someone should be trying to sort the issue to protect the brand from bad PR.
I was nice enough to add art.com’s Twitter account @artdotcom as part of the Tweets made about this issue.
Not tested a Tweet link inside a comment, but the image below should be Tweeted if the “Tweet Above Image” link below it is clicked and it includes reference to @artdotcom.
Tweet Above Image
When I Tweeted about this (several times) their Twitter account would receive a notification. Or if any one at art.com searched for @artdotcom on Twitter (something big businesses should check on a regular basis) they’d find my Tweets.
Come on art.com, pull your finger out and delete the compromised webpages and fix whatever exploit is open on your membership section.
David Law